8 min read
9 Cybersecurity Budget Tips that Deliver the Most Bang for Your Buck
It’s budget time and many organizations are wondering how to allocate their cybersecurity dollars for 2023. As we see it, the ultimate goal of your...
5 min read
 LMG Security
:
Posted on June 13, 2023
LMG Security
:
Posted on June 13, 2023
In today's connected world, mobile phones have become an integral part of our lives. They provide us with convenience, communication, and a wealth of information at our fingertips. However, this increased connectivity comes with inherent security risks. As our reliance on mobile phones grows, so does the need to protect our personal and sensitive data from potential threats. To help you keep your organization safe, let’s dive into the current threat landscape, popular forms of mobile device deployment, and a checklist of mobile device security best practices.
Why are we so concerned about mobile device security? Today’s smartphones are likely to be officially or unofficially used for work since almost ¾ of employees work remotely at least part of the time. In fact, one recent report found that 85% of employers require employees to install work apps (often an authentication app) on their personal devices. This report also found that 71% of employees store sensitive work passwords on their personal phones. So, regardless of whether your organization has a formal BYOD policy, it’s likely that your organization’s passwords and data can be found on employee phones and personal devices. That means one mobile device breach could compromise your security.
The major Uber breach in 2022 started from a contractor’s infected personal device and led to a full network takeover. It’s important that you consider which of the four common mobile device deployment policies is the best fit for your organization, as each approach offers varying levels of flexibility, control, security, and costs. Choosing the most suitable approach depends on factors such as your organization's security requirements, industry regulations, and employee needs. Here’s a brief overview of policy categories:
As criminals increasingly target mobile devices to gain access to the employer’s network, here’s an overview of the common attack methods:
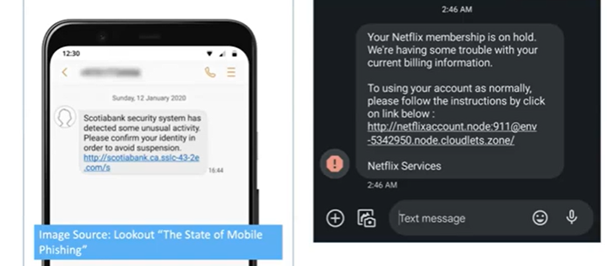 Image source: Lookout
Image source: LookoutThe best way to avoid these mobile device risks is to follow mobile device security best practices and upgrade to secure MFA such as biometrics, authentication apps, or hardware tokens, rather than text or email MFA codes that can be more easily intercepted. For more information on safer MFA, you can also watch our on-demand Beyond Passwords webinar.
Having a mobile security plan is crucial in today’s digital world. Ensure you incorporate these mobile device security best practices in your organization’s cybersecurity plans and policies:

8 min read
It’s budget time and many organizations are wondering how to allocate their cybersecurity dollars for 2023. As we see it, the ultimate goal of your...

A Step-by-Step Guide to Understanding a Network Takeover How do cybercriminals break into a law firm? It can be startlingly quick and easy. We’re...

4 min read
I will admit that, at times and with topics such as cyber security, I can come across as overbearing to some and as a fearmonger to others. Speaking...